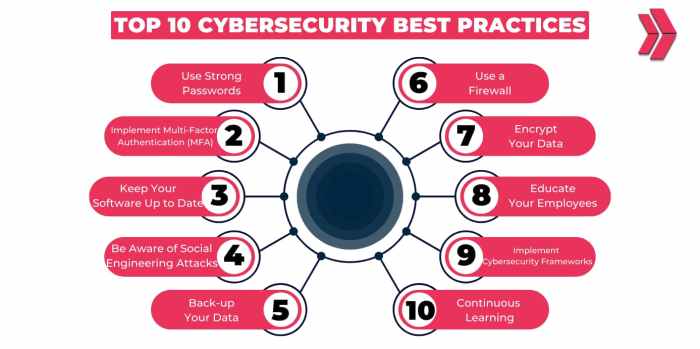
Embark on a journey through the realm of cybersecurity best practices, where the importance of safeguarding digital assets takes center stage. As we navigate recent cyber threats and delve into strategies for fortifying defenses, the significance of proactive cybersecurity measures becomes abundantly clear.
Exploring the nuances of strong password policies, network security measures, employee training, data backup, software updates, and more, this guide equips you with the knowledge to navigate the complex landscape of cybersecurity with confidence.
Importance of Cybersecurity Best Practices
In today's digital landscape, cybersecurity best practices are more crucial than ever. With the increasing reliance on technology for various aspects of our lives, the need to protect sensitive information and systems from cyber threats is paramount.Recent examples of cyber threats, such as ransomware attacks on major organizations or data breaches resulting in the exposure of personal information, highlight the real and present danger posed by cybercriminals.
These incidents serve as a wake-up call for individuals and businesses to prioritize cybersecurity measures to safeguard their digital assets.Neglecting cybersecurity best practices can have severe consequences, ranging from financial losses and reputational damage to legal liabilities. A single security breach can lead to significant disruptions in operations, loss of customer trust, and even regulatory fines.
The aftermath of such incidents can be costly and time-consuming to resolve, underscoring the importance of proactive cybersecurity measures to prevent such scenarios.
Examples of Recent Cyber Threats
- WannaCry ransomware attack that affected over 200,000 computers in 150 countries.
- Equifax data breach that exposed the personal information of 147 million people.
- Phishing attacks targeting individuals and businesses to steal sensitive data.
Implementing Strong Password Policies
Creating and maintaining strong password policies is crucial in ensuring the security of your online accounts and sensitive information. Strong passwords are the first line of defense against cyber threats and unauthorized access.
Characteristics of Strong Passwords
- Use a combination of letters (uppercase and lowercase), numbers, and special characters.
- Avoid using easily guessable information such as birthdays, names, or common words.
- Make passwords at least 12-16 characters long to increase complexity.
- Consider using passphrases that are easy for you to remember but difficult for others to guess.
Creating Unique and Secure Passwords
- Do not reuse passwords across multiple accounts. Each account should have a unique password.
- Consider using a password manager to generate and store complex passwords securely.
- Change default passwords immediately after setting up a new account or device.
- Avoid sharing passwords with anyone, including friends or family members.
Importance of Regular Password Updates and Multi-Factor Authentication
- Regularly update your passwords to prevent unauthorized access, especially after data breaches or security incidents.
- Enable multi-factor authentication (MFA) whenever possible to add an extra layer of security to your accounts.
- MFA requires a second form of verification, such as a code sent to your phone, in addition to your password.
- By implementing MFA, even if your password is compromised, attackers will still need the second factor to access your account.
Network Security Measures
In today's interconnected world, network security is crucial to protect sensitive data and prevent unauthorized access. Implementing effective network security measures can help safeguard your organization against cyber threats.
Network Segmentation
Network segmentation involves dividing a network into smaller subnetworks to enhance security. By separating different parts of the network, organizations can limit the impact of a potential security breach. This practice helps contain threats and prevents attackers from moving laterally within the network.
Firewalls, IDS, and IPS
- Firewalls act as a barrier between a trusted internal network and untrusted external networks, filtering incoming and outgoing traffic based on predefined security rules.
- Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity or security policy violations and generate alerts for further investigation.
- Intrusion Prevention Systems (IPS) go a step further by actively blocking or preventing malicious traffic based on predefined rules.
Securing Wireless Networks
When securing wireless networks, consider the following best practices:
- Change default passwords and SSIDs to unique, strong credentials.
- Enable encryption like WPA2 or WPA3 to protect data in transit.
- Disable SSID broadcasting to make the network less visible to potential attackers.
- Implement MAC address filtering to only allow authorized devices to connect.
- Regularly update firmware and software to patch known vulnerabilities.
Employee Training and Awareness
Employee training and awareness are crucial aspects of cybersecurity in any organization
Common Social Engineering Tactics
- Phishing: Attackers send deceptive emails or messages to trick employees into revealing sensitive information or clicking on malicious links.
- Pretexting: Scammers create a fake scenario to manipulate employees into disclosing confidential information.
- Tailgating: Unauthorized individuals follow employees into restricted areas by pretending to be legitimate personnel.
It is important for employees to be cautious and verify the authenticity of requests before sharing any sensitive information.
Recognizing Social Engineering Tactics
- Encourage employees to verify the sender's email address before opening any attachments or clicking on links.
- Train employees to look out for urgent or threatening language in messages, as these are common tactics used by scammers.
- Remind employees to report any suspicious activities or requests to the IT department immediately.
Regular security training sessions can help employees recognize social engineering tactics and respond appropriately to protect company data.
Data Backup and Recovery
Regular data backups are crucial in mitigating the risks of data loss in the event of a cybersecurity incident. By backing up your data regularly, you ensure that you have a copy of your important information stored securely, allowing you to recover it in case of accidental deletion, hardware failure, or a cyber attack.
Different Backup Methods
- Cloud Backups: Storing your data in the cloud offers convenience and accessibility. Services like Dropbox, Google Drive, or Microsoft OneDrive provide secure storage options with automatic backup features.
- Offline Backups: Utilizing external hard drives, USB drives, or network-attached storage (NAS) devices for offline backups ensures that your data is physically disconnected from your network, reducing the risk of cyber threats.
Creating a Robust Data Recovery Plan
- Identify Critical Data: Determine which data is crucial for your business operations and prioritize its backup.
- Automate Backup Processes: Set up automated backup schedules to ensure consistent and up-to-date copies of your data.
- Test Your Backups: Regularly test your backups to verify their integrity and ensure they can be successfully restored in case of an emergency.
- Implement Access Controls: Restrict access to backup files to authorized personnel only to prevent unauthorized tampering.
- Incident Response Plan: Develop a comprehensive data recovery plan that Artikels steps to take in the event of a cybersecurity incident, including data restoration procedures.
Regular Software Updates and Patch Management
Keeping software up to date with the latest security patches is crucial in maintaining a secure IT environment. These updates often address vulnerabilities that cybercriminals can exploit to gain unauthorized access to systems or steal sensitive data.
Importance of Patch Management
Implementing a patch management strategy within an organization is essential to ensure that all software and applications are regularly updated with the latest patches. Failure to do so can lead to various risks and security threats.
- Increased Vulnerabilities: Running outdated software exposes systems to known security vulnerabilities that can be easily exploited by hackers.
- Data Breaches: Without timely patches, organizations are at a higher risk of experiencing data breaches, resulting in financial losses and reputational damage.
- Compliance Violations: Many industry regulations and standards require organizations to maintain up-to-date software to protect sensitive information. Failing to do so can lead to compliance violations and penalties.
Best Practices for Patch Management
Here are some best practices for implementing a patch management strategy:
- Automate Patch Deployment: Utilize patch management tools to automate the deployment of patches across all systems and devices.
- Prioritize Critical Patches: Focus on critical security patches that address vulnerabilities posing the highest risk to the organization.
- Test Patches Before Deployment: Before deploying patches, test them in a controlled environment to ensure they do not cause any compatibility issues or system disruptions.
- Establish Patching Policies: Create clear policies and procedures for patch management, including regular patching schedules and maintenance windows.
- Monitor Patch Compliance: Regularly monitor patch compliance to ensure that all systems are up to date and protected against known vulnerabilities.
Final Conclusion
In conclusion, embracing cybersecurity best practices is not merely a choice but a necessity in today's interconnected world. By implementing robust security measures, staying vigilant against evolving threats, and fostering a culture of cyber awareness, individuals and organizations can effectively mitigate risks and safeguard sensitive information.
Commonly Asked Questions
How often should passwords be updated?
Passwords should ideally be updated every 90 days to maintain security.
What are some common social engineering tactics?
Common social engineering tactics include phishing emails, pretexting, and baiting.
Why is network segmentation important for cybersecurity?
Network segmentation limits the scope of potential breaches by dividing networks into smaller, more manageable sections.
How can organizations create a robust data recovery plan?
Organizations can create a robust data recovery plan by regularly backing up data, testing recovery procedures, and ensuring backups are stored securely.
What risks are associated with running outdated software?
Running outdated software exposes systems to vulnerabilities that can be exploited by cyber attackers.